LDAP access to MCommunity Directory data is provided via the MCommunity LDAP Tree. The LDAP Tree is an LDAP-accessible replica of the directory. This document provides general information about the MCommunity LDAP Tree, including a list of the most frequently used attributes.
If you are looking for information about LDAP access to Active Directory, see Understanding LDAP and Global Catalog Access to the UMROOT Active Directory.
What is LDAP Used for?
Staff members in many units throughout the university currently use LDAP command-line tools to work with directory data. LDAP is also used by various services and applications at U-M for user authorization. LDAP users can connect to the MCommunity LDAP Tree for LDAP access to MCommunity data.
If you need to work with MCommunity Directory data in ways that are not outlined here, please contact the ITS Service Center for assistance. Other data access options may be available to meet your university business needs.
Note Research projects using directory data (even public directory data) could be considered "human subject" research. Such research requires approval from U-M's Institutional Review Board. Students should consult with their faculty advisor.
Authenticated Versus Unauthenticated Access
Unauthenticated Access: If you require access to data in MCommunity that is publicly available, you do not need to authenticate if you are not writing to the directory. You can use anonymous access.
Authenticated Access: In order to write to the directory via LDAP, or read data that has been hidden from public access in MCommunity, you or your application will need to authenticate.
- Authenticated access: You can authenticate with your uniqname and UMICH password to read information that would otherwise be hidden and to make changes to your own profile and groups.
- Authenticated administrative access: To read information about people or groups that would otherwise be hidden, or to make changes to groups programmatically, your department will need to request administrative access. In limited cases, departments can also be permitted to make changes to other people's entries (for example, to set their mail forwarding address for them). To request administrative access, contact the ITS Service Center. See configuration details below.
Configuration
Host name: ldap.umich.edu
Search path: dc=umich, dc=edu
Port number: 389
Using Simple Bind (with uniqname and UMICH Password)
You are required to secure your connection when performing a simple bind. Download and install the appropriate certificate as described below. A secure connection can then be obtained using either
-
TLS on Port 389 by including -ZZ to start Transport Layer Security (TLS)
-
SSL on Port 636 by using host name ldaps://ldap.umich.edu
Using a Non-Person ID for Programmatic Access
If you are using a non-person ID for programmatic access (available from the ITS Service Center), you will need to install a certificate so that you can use an encrypted connection. See instructions below.
Installing and Configuring Certificates
You will need to download the certificate from the InCommon Certificate Service.
-
Go to the InCommon Cert Types page.
-
Under the SSL/TLS Certificates heading, under the Organizational Validation SSL/TLS Certificates subheading, click the [PEM] link for AddTrust External CA Root.
Installation and configuration instructions depend on the LDAP client you are using. Check your LDAP client documentation for instructions.
LDAP Write Access Changes
You can make changes to your own profile and the profiles of groups that you own in the MCommunity Directory via LDAP. You may also be able to make changes to other people's profiles and groups if you have administrative access.
The following attributes can be changed via LDAP:
Individual Profiles
- mailForwardingAddress
- RealtimeBlocklist
- associatedDomain
Group Profiles
- owner
- member
- errorsTo
- requestsTo
- rfc822ErrorsTo
- rfc822RequestsTo
- rfc822mail
- groupMember
- umichRenew
Other attributes must be changed using the web interface. For details about these and other attributes, see MCommunity Attributes below. If you need to work with MCommunity Directory data in ways other than described here, please contact the ITS Service Center for assistance. Other data access options may be available to meet your university business needs.
Access Is Via a Replica
The MCommunity Directory will not be available directly via LDAP. Instead, LDAP access to the directory data will be provided by an MCommunity LDAP Tree—an LDAP-accessible replica of the directory. The diagram below shows the relationship between the LDAP Tree and the actual directory. Drivers populate the LDAP Tree from the directory and send changes back to the directory in real time.
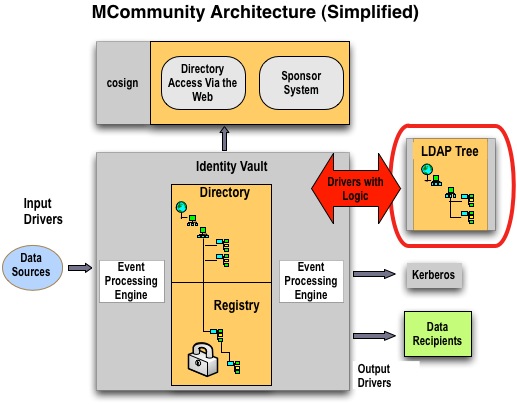
The drivers contain logic to enforce MCommunity's data policies. Because LDAP does not allow for implementation of complex data policies, LDAP users may make a seemingly successful change to the LDAP Tree that is rejected by a driver upon population to the directory. For example, if you enter an improperly formatted e-mail address into an attribute, LDAP will not stop you. The drivers, however, notify you via email that you should correct the address and try again.
Interpreting the Data
Data housed in the MCommunity Directory and LDAP Tree comes from multiple different authoritative data sources, including the M-Pathways Human Resource Management System, the M-Pathways Student Administration database, the Dearborn Banner system, the Flint Banner System, the Donor Alumni Relations Tool (DART) database, and the MCommunity Sponsor System.
Before writing an LDAP query, units should understand the data provided by these sources. When querying Human Resources data, for example, you should first consult with your local Human Resources staff to understand the jobcodes, department IDs, and HR business practices that are relevant to your unit.
MCommunity Attributes
The attributes most likely to be accessed via LDAP are provided in these formats:
- A web-accessible table (view MCommunity attributes)
- A PDF file for printing (Download MCommunityAttributesforLDAP.pdf)
- An Excel spreadsheet (so you can copy and paste only the attributes you need Download MCommunityAttributesforLDAP.xlsx)
